[ad_1]
Decoding Cryptoprogram: Unveiling the Secrets of Modern Encryption
In a world that is increasingly interconnected, the need for secure communication has become paramount. Governments, corporations, and individuals alike rely on encryption to protect their data from prying eyes. But how does encryption work, and what are the secrets behind modern cryptosystems?
Encryption, at its core, is the process of converting plain text into a format that is unintelligible to unauthorized entities. Over the centuries, different methods have been used to achieve this. From Caesar ciphers in ancient Rome to the Enigma machine of World War II, encryption has evolved alongside advancements in technology.
However, modern encryption relies on mathematical algorithms and computational complexity to ensure its security. Two key components underpin modern encryption: asymmetric encryption and symmetric encryption.
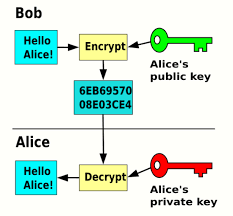
Asymmetric encryption, also known as public-key encryption, utilizes a pair of keys — a public key and a private key. The public key is openly shared, allowing anyone to encrypt a message, while the private key is kept secret, allowing only the intended recipient to decrypt the message.
This encryption method is based on the difficulty of certain mathematical computations, such as factoring large numbers. For example, the widely used RSA algorithm relies on the assumption that it is computationally infeasible to factorize a large number into its prime factors. By exploiting this mathematical property, secure communication can be achieved.
On the other hand, symmetric encryption employs a single key to both encrypt and decrypt the data. This shared key must be kept secret between the sender and the recipient. The Advanced Encryption Standard (AES) is a widely adopted symmetric encryption algorithm, known for its efficiency and security.
While the fundamentals of encryption are crucial for secure communication, cryptanalysis focuses on breaking the encryption. Cryptanalysts employ various techniques, including code-breaking, brute-force attacks, and side-channel attacks to try and uncover the plaintext from the encrypted message.
Code-breaking involves analyzing the structure of the encryption algorithm itself and finding vulnerabilitie
s that could be exploited. This technique requires a deep understanding of the mathematical foundations of encryption and often involves complex mathematical computations.
Brute-force attacks, as the name suggests, involve systematically trying every possible key until the correct one is found. With the increasing power of computers, brute-forcing encryption keys has become more feasible, but it is still highly resource-intensive and time-consuming.
Side-channel attacks target the implementation of the encryption algorithm, rather than the algorithm itself. By analyzing unintended information leaks, such as power consumption or electromagnetic emissions, attackers can gain insights into the encryption key.
The cat-and-mouse game between cryptographers and cryptanalysts has led to a constant evolution of encryption algorithms. As vulnerabilities are discovered, new encryption methods, protocols, and standards are developed to ensure continued security.
The concept of “quantum-resistant cryptography” has gained attention in recent years. Quantum computers, unlike classical computers, are capable of performing certain mathematical computations much faster. If built at a sufficient scale, quantum computers could potentially break many of the existing encryption algorithms. To counter this, researchers are actively working on developing encryption methods that are resistant to quantum attacks.
While encryption provides a critical layer of security, it is not foolproof. Encryption systems rely on the integrity of the keys and the implementation of the algorithms. Weak keys, poorly implemented protocols, or flawed implementations can all compromise the security of the encrypted data.
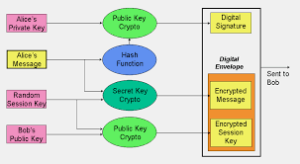
Moreover, encryption is often accompanied by additional security measures, such as authentication and digital signatures, to ensure the integrity and authenticity of the data. Encryption is just one piece of the puzzle in a holistic approach to securing communication and information.
Tectonic Crypto Price Prediction 2025: Experts Anticipate Major Market Shakeups
In conclusion, encryption plays a vital role in safeguarding our information in an increasingly digital world. The secrets behind modern encryption lie in complex mathematical algorithms and the continuous efforts of researchers to ensure its security. Understanding the fundamentals of encryption and its vulnerabilities empowers us to protect our data and communicate securely. As technology advances, encryption will continue to evolve, and staying one step ahead of potential adversaries will be crucial in ensuring the confidentiality and integrity of our digital lives.
[ad_2]





