[ad_1]
Cryptology and cryptography are two terms that are often used interchangeably, leading to confusion for many people. While they are both related to the field of secure communication, there are subtle differences between the two. This article aims to demystify these differences and provide a clear understanding of cryptology and cryptography.
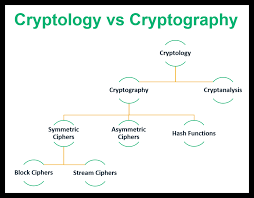
Cryptology is a broad term that encompasses the study of techniques for secure communication. It includes cryptography, which is the practice of creating codes and ciphers to secure information, as well as cryptanalysis, which focuses on breaking codes and decrypting encrypted messages. In simple terms, cryptology is the umbrella term that encompasses both cryptography and cryptanalysis.
Cryptography, on the other hand, is the specific practice of creating codes and ciphers to secure information. It involves techniques for encrypting and decrypting messages, ensuring that only authorized individuals can access the information. Cryptography relies on mathematical algorithms and key-based systems to provide confidentiality, integrity, and authentication for digital communication.
The goal of cryptography is to create secure systems that protect information from unauthorized access or tampering. It achieves this by converting plaintext information into ciphertext, which is unintelligible to anyone except the intended recipient who possesses the decryption key. Cryptographic systems provide various levels of security, depending on the encryption algorithms and the length of the encryption keys used.
There are two main types of cryptography: symmetric key cryptography and asymmetric key cryptography. Symmetric key cryptography uses the same key for both encryption and decryption. This means that the sender and the recipient must have the same key, and securely sharing this key is a significant challenge. On the other hand, asymmetric key cryptography uses different keys for encryption and decryption. This eliminates the need to share a secret key, as each user has a public key for encryption and a private key for decryption.
How Legitimate Crypto Recovery Companies Help Investors Retrieve Stolen Funds Safely
Cryptanalysis, the counterpart to cryptography, is the practice of breaking codes and decrypting encrypted messages. It involves analyzing cryptographic systems to identify weaknesses and vulnerabilities that can be exploited to retrieve the original information. Cryptanalysis techniques include brute force attacks, frequency analysis, and statistical methods. Cryptanalysts play a crucial role in evaluating the security of cryptographic systems and developing more robust encryption algorithms.
Both cryptology and cryptography have evolved significantly over the years, driven by the need for secure communication in an increasingly digital world. With the rise of the internet and the widespread use of digital technologies, the protection of sensitive information has become a critical concern. Cryptography provides the foundation for various applications, such as secure online transactions, secure messaging, and secure storage of sensitive data.
Understanding the difference between cryptology and cryptography is essential for anyone interested in the field of secure communication. While cryptology encompasses the broader study of secure communication techniques, cryptography focuses specifically on the creation of codes and ciphers to secure information. Cryptanalysis complements cryptography by analyzing and breaking cryptographic systems to improve their security.
In conclusion, cryptology and cryptography are two related but distinct terms within the field of secure communication. Cryptology is the broader study of techniques for secure communication, while cryptography is the specific practice of creating codes and ciphers to secure information. Both are crucial in ensuring the confidentiality, integrity, and authentication of digital communication systems. The evolution of these fields will continue to play a vital role in safeguarding sensitive information in the digital era.
[ad_2]