[ad_1]
Understanding Cryptographic Entropy: The Key to Securing Digital Communications
In our increasingly digital world, securing communication has become a crucial aspect of everyday life. Whether it’s protecting personal data during online transactions or safeguarding sensitive information in corporate communications, cryptographic algorithms play a vital role in ensuring the confidentiality, integrity, and authenticity of digital communications. One of the fundamental concepts in cryptography is cryptographic entropy – a measure of the unpredictability and randomness of cryptographic keys. In this article, we will delve deeper into the concept of cryptographic entropy and explore its significance in securing digital communications.
What is Cryptographic Entropy?
Entropy, as defined in thermodynamics, relates to the measure of disorder or randomness in a system. In the context of cryptography, cryptographic entropy refers to the randomness or unpredictability of the data used to generate cryptographic keys. It is a critical factor in determining the security strength of encryption algorithms.
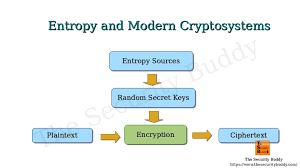
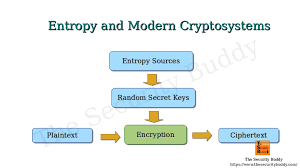
Cryptographic keys are crucial to the security of cryptographic systems. Used for encryption and decryption, they need to be generated in a manner that is highly unpredictable to ensure the security of encrypted data. If a key is predictable or can be easily guessed, an attacker could potentially decrypt the protected information.
Exploring the Magical World of Cryptocrystalline Quartz: A Closer Look at its Mystical Properties
Generating Cryptographic Keys
The process of generating cryptographic keys relies heavily on the availability of true randomness or sufficient entropy. However, true randomness is difficult to achieve in digital systems, which operate on deterministic algorithms. Instead, cryptographic systems rely on pseudorandom number generators (PRNGs) to generate keys.
Pseudorandom Number Generators
Pseudorandom number generators use deterministically generated seed values to produce a sequence of seemingly random numbers. These PRNGs are widely used in computer systems due to their efficiency and speed. The choice of a secure PRNG is crucial to the overall security of cryptographic systems.
To ensure the cryptographic entropy of keys generated by PRNGs, they must be periodically seeded with fresh entropy. This can be achieved by collecting random data from various sources, such as mouse movements, keyboard timings, or measured electronic noise.
Entropy Sources
Entropy sources are fundamental to the security of cryptographic systems. They are responsible for providing the required amount of randomness to generate cryptographic keys. There are two types of entropy sources:
1. Physical Entropy Sources: These sources extract randomness from physical phenomena, such as electrical noise, radioactive decay, or atmospheric noise. The unpredictability of these natural phenomena ensures the randomness of the collected data. Hardware-based random number generators often make use of physical entropy sources.
2. Software Entropy Sources: Software entropy sources are mainly used in situations where hardware randomness is not readily available. They rely on collecting data from various system events, such as disk activity, network traffic, or user input, to generate entropy. However, it is crucial to validate the collected data to ensure it has sufficient entropy.
Evaluating Cryptographic Entropy
Evaluating the quality and strength of cryptographic entropy is essential to ensure the security of cryptographic systems. Several statistical tests and metrics are used to evaluate the entropy of generated keys, such as the Frequency Test, Runs Test, and Entropy per Byte.
Additionally, cryptographic algorithms, such as the Advanced Encryption Standard (AES) or the RSA algorithm, have specific requirements for the length and randomness of cryptographic keys. Meeting these requirements ensures the strength of cryptographic systems.
Importance of Cryptographic Entropy
Cryptographic entropy is vital for maintaining the security of digital communications. Without sufficient entropy, cryptographic keys become predictable, rendering encryption algorithms vulnerable to attacks. Adversaries could employ brute force attacks or exploit patterns in key generation to compromise sensitive communications.
Furthermore, maintaining a high level of cryptographic entropy is crucial for long-term security. As computational power and attack techniques improve, what was once considered a secure key length might become vulnerable over time. Therefore, regularly updating and refreshing cryptographic keys with newly generated entropy is crucial to ensuring ongoing security.
Conclusion
Cryptographic entropy plays a critical role in securing digital communications. Understanding the importance of generating and evaluating cryptographic entropy is essential for ensuring the confidentiality and integrity of sensitive information. As technology continues to advance, the need for robust encryption systems that rely on unpredictable keys becomes increasingly important. By embracing cryptographic entropy and its significance, we can strive for stronger and more secure digital communications in our interconnected world.
[ad_2]